In the dynamic landscape of cybersecurity, the need for robust Vulnerability Assessment and Penetration Testing tools is more crucial than ever. With the ongoing trend towards more agile release cycles and compact sprints, the need to address the security assessment increases and seamlessly integrate them in the Continuous Integration/Continuous Deployment (CI/CD) pipeline.
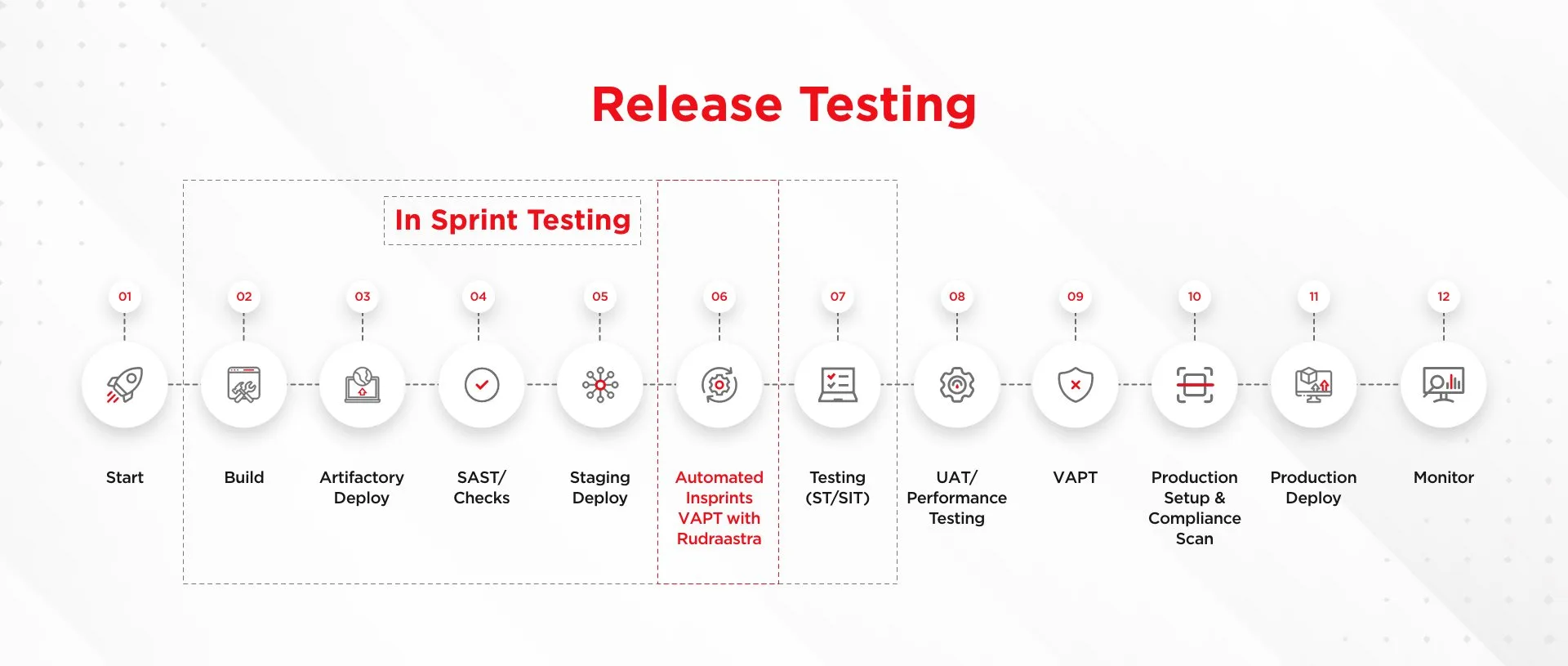
Traditionally, Vulnerability Assessment and Penetration Testing (VAPT) encompasses key stages—Reconnaissance, Scanning, Vulnerability Assessment, Exploitation, and Reporting.
Various enterprise tools available in the market for security testing cover all these stages but they do have coverage gaps, necessitating the use of supplementary open-source tools. Also, integrating these enterprise tools into the CI/CD pipeline can be cost-prohibitive for companies. On the flip side, open-source tools can address specific vulnerabilities individually and require manual execution. Complicating matters, each tool tends to focus on distinct types of vulnerabilities, compelling the need for a combination of tools. Unfortunately, integrating this diverse set of open-source tools into the CI/CD pipeline proves to be impossible.
RudraAstra steps in as an adept solution. Thoughtfully curated and meticulously crafted with a combination of open-source tools and frameworks to cover the maximum phases of the security assessment. RudraAstra helps in automating the entire workflow, making seamless integration with Jenkins CI/CD pipelines a reality. This initiative is poised to refine and streamline the testing process within the intricate landscape of the development life cycle.
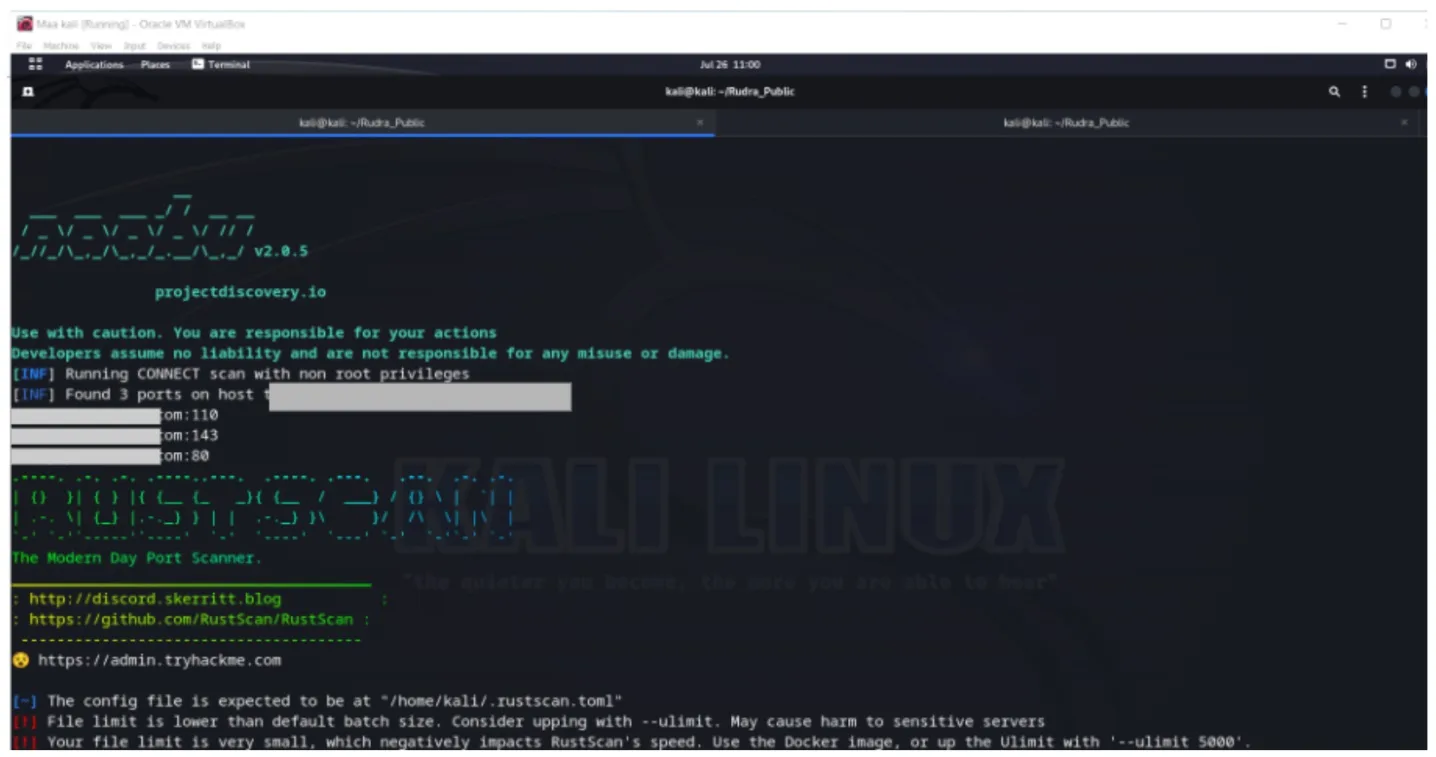
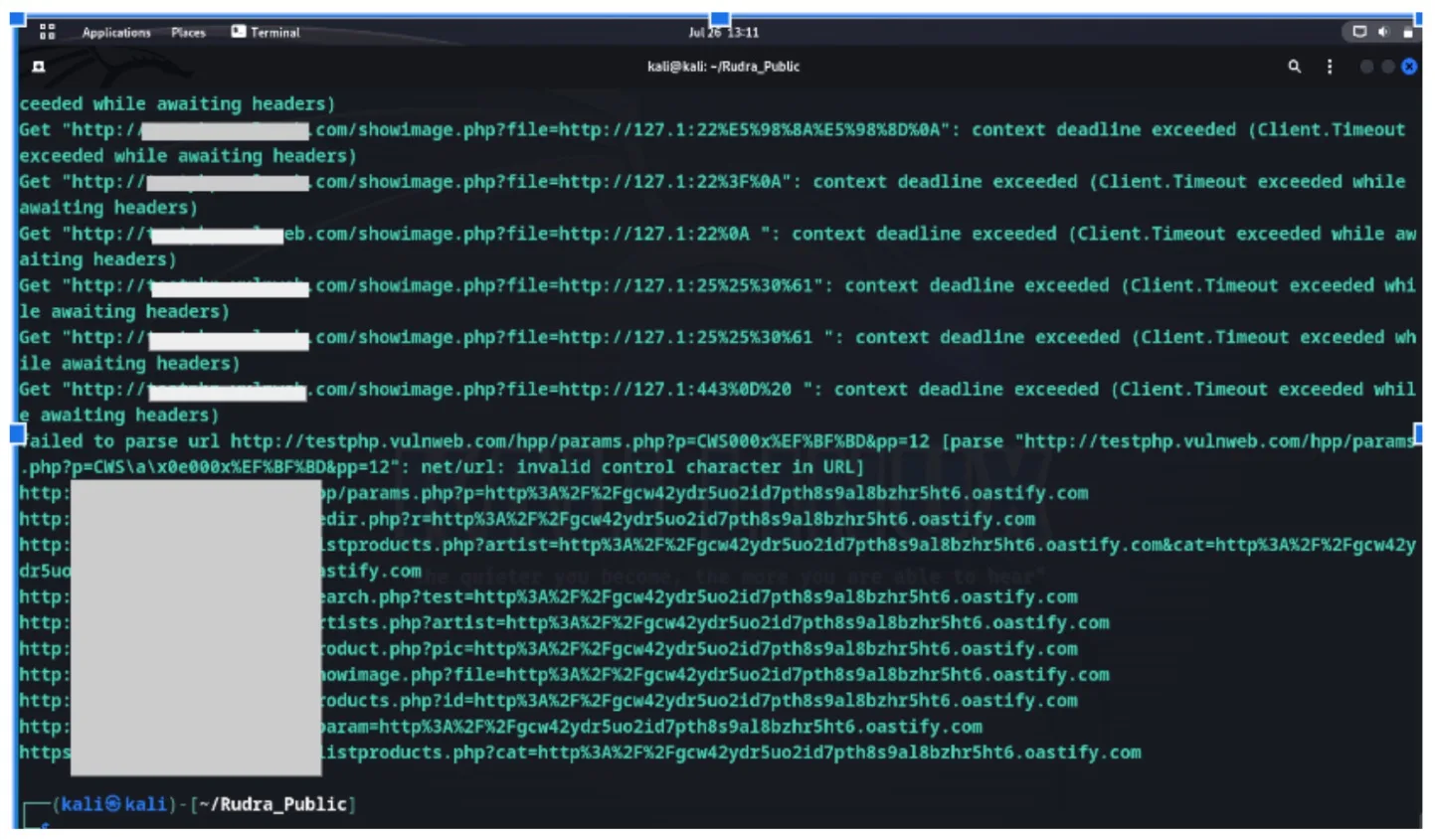
RudraAstra is a comprehensive bash script amalgamating multiple open-source tools and frameworks, purposefully designed to facilitate VAPT. It seamlessly navigates through the VAPT life cycle, commencing with Scanning and Reconnaissance. RudraAstra autonomously gathers information, analyzes target applications, identifies open ports, discovers directories, pinpoints sensitive API endpoints, and fetches details about web technologies, services, and OS data. The script seamlessly transitions into Vulnerability Assessment, meticulously scanning for security flaws.
Subsequently, it engages in ethical Exploitation, addressing vulnerabilities such as XSS, SQL, CRLF, Host Header Injection, and Command Injections. Post-scanning, RudraAstra delivers structured results in a text file, organized by folders, each containing comments for efficient collaboration and remediation efforts. The automation embedded within RudraAstra streamlines the entire process, enhancing the effectiveness and efficiency of VAPT procedures.
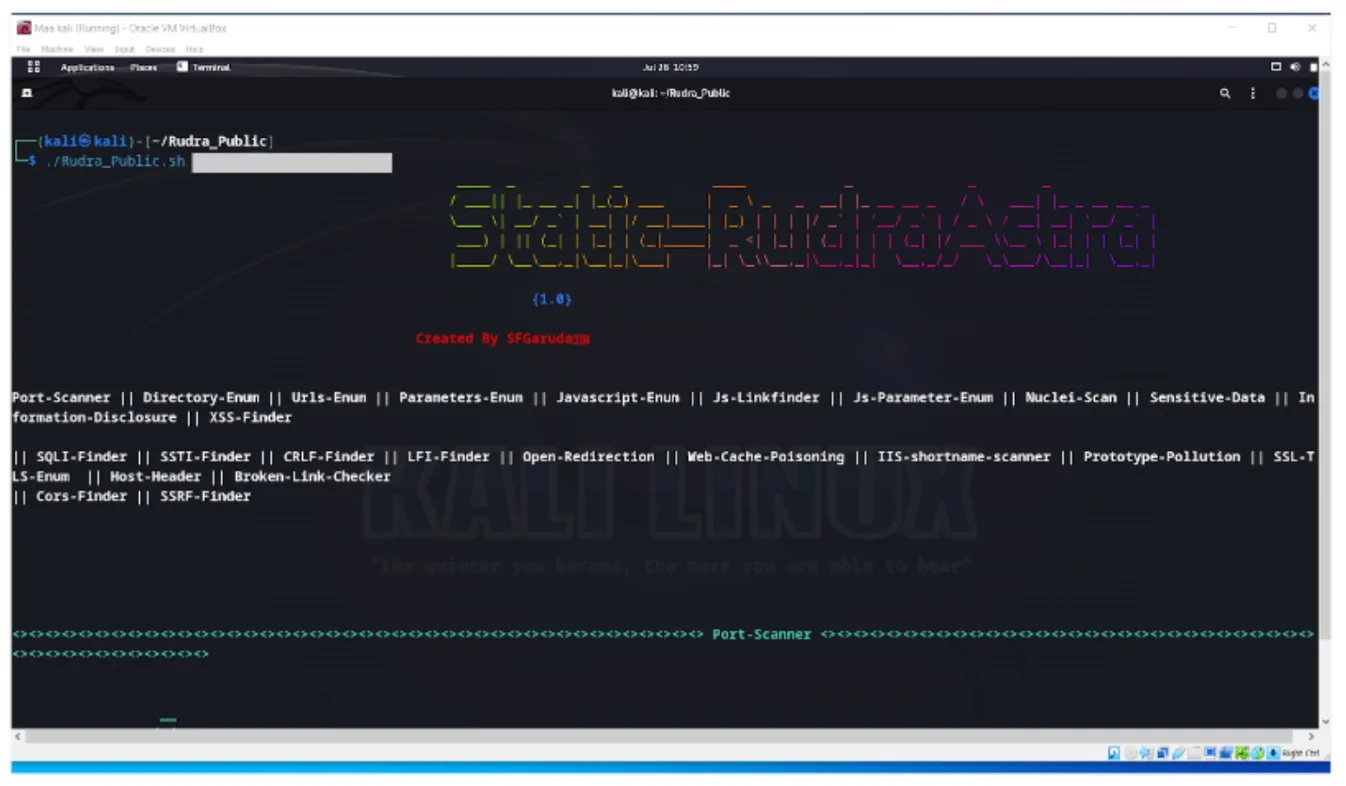

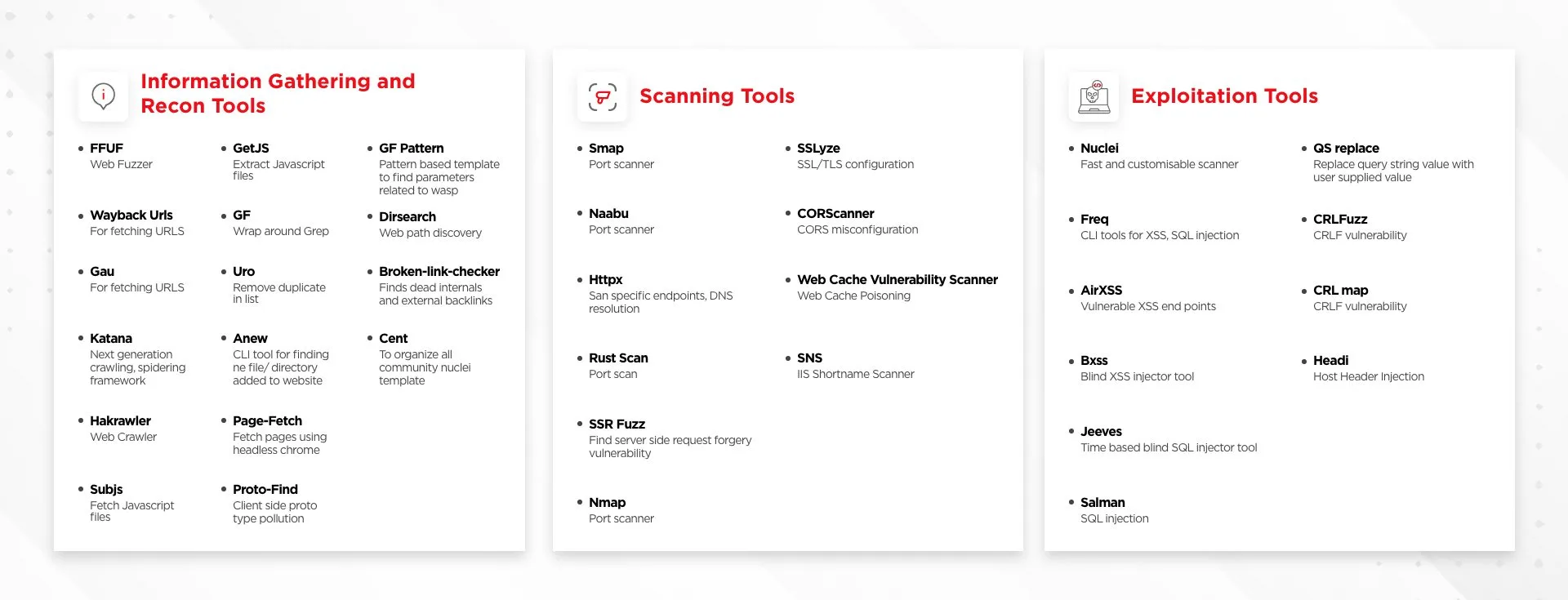
Tools Integrated in RudraAstra:
Features of RudraAstra
- Comprehensive Coverage of Testing: RudraAstra seamlessly navigates through each phase offering end-to-end coverage from code deployment to initial mapping and information gathering to exploitation. This tool amalgamates various frameworks and tools, ensuring a holistic approach to security testing.
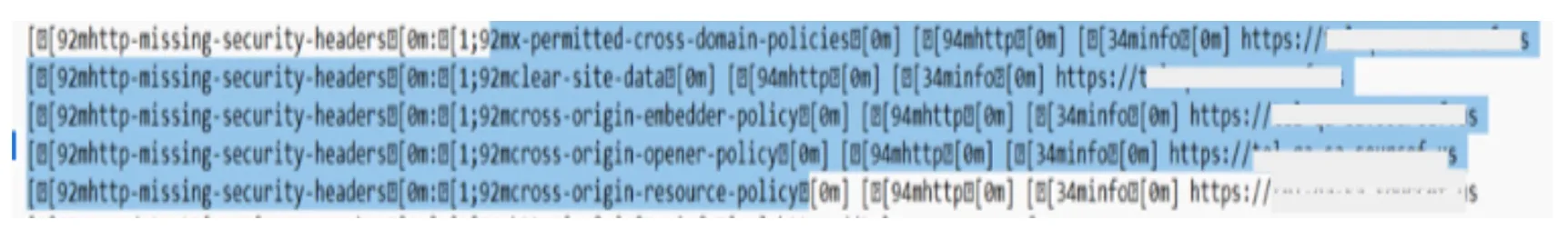
- Specialized Frameworks for Identification of Unique Features: The framework not only streamlines the identification of API lists but also orchestrates a comprehensive Common Vulnerabilities and Exposures (CVE) scan. In this way, it uniquely offers detailed insights into potential vulnerabilities.
- Upgrade and Updates: A key feature of RudraAstra is its adaptability. Regular upgrades and updates ensure that the tool stays current with evolving security landscapes, making it a reliable asset without the need to invest in maintaining robust cybersecurity measures.
- Integration with Jenkins CI/CD Pipeline: By seamlessly integrating into a Jenkins pipeline, RudraAstra helps in detecting vulnerabilities early in the process. This is unlike the conventional approach of identifying bugs only at the end in Dynamic Application Security Testing. This proactive approach allows for swift bug resolution and bolsters the overall security posture.
Advantages of RudraAstra
- Early Vulnerability Detection:
The challenge of identifying vulnerabilities early in the development process is met by RudraAstra’s integration. Automated security scans at every stage of the CI/CD pipeline enable the ability to catch potential issues before they escalate, ensuring a proactive response to security threats. - Time and Manpower Saving:
In the traditional approach, testers are required to navigate through multiple windows to execute individual tools, resulting in a lengthy and cumbersome process. The consolidation of various tools within RudraAstra empowers users by executing multiple tools simultaneously, significantly saving time and effort. This eliminates the need for the previously time-consuming practice of executing each tool. The tool’s automation not only streamlines repetitive tasks but also ensures quicker assessments, expedited results, consistency, and scalability in VAPT processes. - Reduced Cost of Quality:
Containing costs associated with vulnerability remediation is a common concern. RudraAstra’s automated scans contribute to cost reduction by addressing issues early on, preventing the escalation of vulnerabilities into more complex and costly problems. Indeed, using open-source tools in RudraAstra helps organizations save on licensing costs. - Security as Code Implementation:
Implementing security as code can be a daunting task without the right tools. RudraAstra, integrated seamlessly into the CI/CD pipeline, enables the ability to embed security practices directly into the code, fostering a proactive security culture within the development process. - Continuous Monitoring:
Continuous monitoring is essential for identifying and responding to emerging threats. RudraAstra’s integration ensures that security measures are continuously applied throughout the software development life cycle, providing real-time insights into potential risks. - Collaboration Between Teams:
Bridging the gap between development and security teams is crucial for a successful security strategy. RudraAstra’s integration fosters collaboration by providing a unified platform for both teams to work together seamlessly, sharing insights and addressing vulnerabilities collaboratively.
Conclusion
Mastering the intricacies of early vulnerability detection, continuous monitoring, and fostering collaboration between development and security teams.
In essence, integrating RudraAstra into Jenkins’ CI/CD pipeline not only proves instrumental in overcoming security challenges throughout the software development life cycle; it also plays a pivotal role in aligning security practices with contemporary software delivery processes.
This powerful amalgamation ensures a proactive and robust approach to cybersecurity. By leveraging this combination, not only are current concerns addressed but a collaborative and forward-looking security strategy can be established, ensuring the resilience of applications against evolving threats.