In today’s fast-paced business landscape, the demand for reliable and efficient identity recognition solutions is more critical than ever. Face recognition technology has emerged as a game-changer, offering versatile applications across various industries, from enhancing security protocols to optimizing personalized experiences.
However, implementing robust facial recognition software or machine learning in surveillance that can perform accurately under diverse conditions presents its own set of challenges. In this blog, we’ll explore how our tailored business solution harnesses advanced techniques to deliver seamless identity recognition and verification without delving into technical complexities.
Introduction
Face recognition technology utilizes advanced algorithms to analyze and compare facial features extracted from images or video footage, enabling identification and verification of individuals.
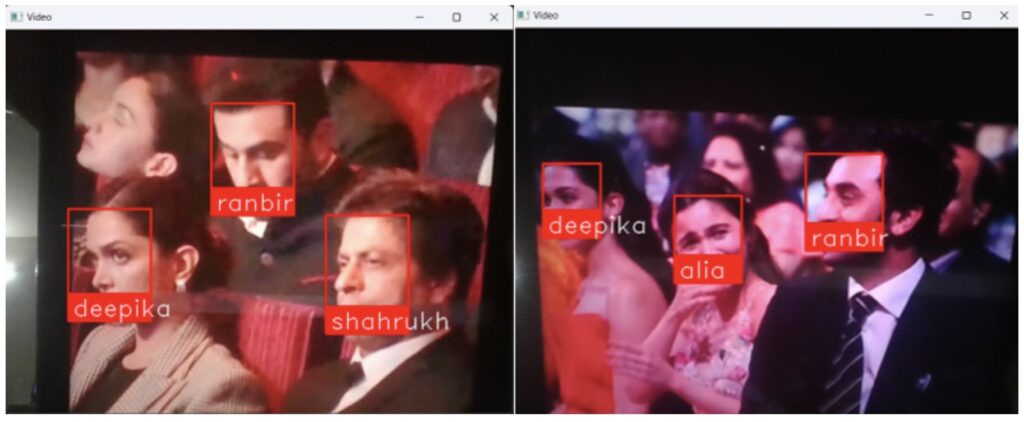
Our Approach
At SourceFuse, we utilize cutting-edge technologies and innovative algorithms for facial detection. Our approach involves several key steps:
1. Tailored Dataset Preparation:
Building a reliable dataset is foundational. We meticulously curate images of known individuals and then enhance this dataset through cropping and augmentation techniques. This step ensures that our system is trained on a diverse range of facial variations, leading to more accurate recognition.
2. Detection of Faces:
Armed with advanced models like MTCNN and DeepFace, we accurately identify faces within images or video streams by extracting rich facial features. This enables precise recognition even in challenging conditions. This initial detection phase sets the stage for subsequent processing, ensuring that no face goes unnoticed.
3. Data Augmentation for Versatility:
Data augmentation techniques such as blur, resize, and random transformations are applied to the extracted face images. These techniques help enrich the dataset, enabling our system to adapt to different lighting conditions, facial expressions, and occlusions.
4. Efficient Encoding and Recognition:
Each face in our training dataset undergoes a meticulous encoding process, where facial features are extracted and converted into numerical vectors. These encoded representations enable rapid and efficient comparison during real time recognition, empowering our system to accurately match faces with known identities.
Benefits of Our Approach
- Improved Accuracy:
- Real Time Recognition:
- Customizable and Extensible:
Applications
- Access Control Systems: Our solution can be integrated into access control systems to enhance security measures in various facilities, including offices, manufacturing plants, and data centers. By accurately identifying authorized personnel, it prevents unauthorized access and strengthens overall security protocols.
- Attendance Tracking: In educational institutions and corporate settings, our solution can streamline attendance tracking processes. By automating the identification of individuals, it eliminates manual entry errors and provides real time attendance updates for administrators.
- Customer Authentication: For businesses operating in the digital space, such as e-commerce platforms and banking institutions, our solution can be utilized for customer authentication purposes. By verifying customer identities accurately and efficiently, it enhances security and prevents fraudulent activities.
- Surveillance and Monitoring: Our solution can serve as a powerful tool for surveillance and monitoring in public spaces, transportation hubs, and retail environments. By continuously analyzing live video feeds, it enables proactive identification of suspicious individuals and enhances overall safety and security.
- Personalized Experiences: In the realm of personalized experiences, our solution can be leveraged to enhance customer interactions in various industries. For example, in hospitality, it can facilitate personalized greetings and services based on recognized guest profiles, enhancing overall satisfaction and loyalty.
- Lost Child Detection: In crowded environments such as amusement parks and shopping malls, our solution can aid in the rapid identification and location of lost children. By quickly scanning crowds and matching faces against a database of registered individuals, it expedites the reunification process and ensures the safety of children.
- Law Enforcement: Our solution can support law enforcement agencies in criminal investigations by aiding in the identification and tracking of suspects. By cross-referencing facial images with databases of known individuals, it helps law enforcement officers to identify potential leads and solve cases more efficiently.
Conclusion
At SourceFuse, we’ve developed a comprehensive approach by integrating these elements into a cohesive framework. Our approach delivers a face recognition solution that excels in accuracy, reliability, and versatility. Whether deployed for security, surveillance, or personalized experiences, our system sets the standard for seamless and effective identity recognition and verification in today’s digital landscape.
Discover advanced techniques to deliver seamless identity recognition with SourceFuse.
*Images used are under Fair Use:
Copyright Disclaimer Under Section 107 of the Copyright Act in 1976; Allowance is made for “Fair Use” for purposes such as criticism, comment, news reporting, teaching, scholarship, and research.
Fair use is a use permitted by copyright statute that might otherwise be infringing.
All rights and credit go directly to its rightful owners. No copyright infringement intended.