In a global economy, virtually every organization is connected to or dependent upon others. Hence, as we work from home during this global pandemic, we can come up with the most effective approach to enable critical systems to work with minimum disruption. Our goal is to maximize productivity as much as we can, while working remotely and bringing our business continuity planning to a successful level.
Given that we are all working from home, the risk of enterprise security breaches, malware, and unauthorized activities is also increased. To make sure that we limit the security risk and ensure best practices while working on the cloud from our homes, SourceFuse, as AWS Advanced Consulting Partners, suggests you follow certain measures.
How to make your platforms more secure?
We are sure you must be using multiple online platforms on a daily basis to get your work done. While it’s great that your tasks are completed on the cloud, there are certain security issues that might pop up now and then. This would be a good time to train your newly minted employees to learn a thing or two about security awareness. Hence, we suggest the following assessment on your systems:
- Notify which clouds & applications are sanctioned for use: Provide a secure way for your employees to access the applications they need. Make sure they use only the ones that are authorized by your security team.
- Make sure the work is within enterprise endpoints: Your employees working from home must have a secured Wi-Fi network and work with a trusted virtual private network (VPN). We advise you to keep your VPN active so that it can help provide a secure link between your employees and clients by encrypting data and scanning devices for malicious software such as viruses and ransomware.
- Enable multi-factor authentication: Consistently implement multi-factor authentication (MFA) for AWS service management, on login and privilege elevation for AWS instances, or when checking out vaulted passwords.
- Get a Support Hotline for remote workers: Make sure all your employees are well connected and can contact you in times of connection troubles, and/or otherwise. Ensuring an open door policy will prove effective for your employees and further, for effective business continuity.
Working From Home? Here’s How SourceFuse Can Help
When pursuing cloud migration, there are certain best practices that you need to follow for maximum security and compliance. We are listing some of them below for your ease:
- Amazon WorkSpaces: It lets you launch Virtual Windows and Linux desktops that can be accessed anywhere and from any device. These desktops can be used for remote work, remote training, and more.
- Using the IAM Service for Security: The IAM service is one component of the AWS secure global infrastructure. With IAM, you can centrally manage users, security credentials such as passwords, access keys, and permissions policies that control which AWS services and resources users can access. IAM lets you create individual users within your AWS account and give them each their own user name, password, and access keys.
- Know the AWS Shared Responsibility Model: AWS offers a variety of infrastructure and platform services. For the purpose of understanding security and shared responsibility of these AWS services, they are categorized into: infrastructure, container, and abstracted services.
With Infrastructure Services such as Amazon EC2, Amazon Elastic Block Store (Amazon EBS), Auto Scaling, and Amazon Virtual Private Cloud, you can architect and build a cloud infrastructure using technologies similar to and largely compatible with on-premises solutions.
Container Services such as Amazon RDS and AWS Elastic Beanstalk run on separate Amazon EC2 or other infrastructure instances. You are responsible for setting up and managing network controls, such as firewall rules, and for managing platform-level identity and access management separately from IAM.
Abstracted Services include high-level storage, database, and messaging services, such as Amazon S3, Amazon Glacier, Amazon DynamoDB, Amazon SQS and, Amazon SES. You access the endpoints of these abstracted services using AWS APIs, and AWS manages the underlying service components or the operating system on which they reside.
- Resource Access Authorization: After a user or IAM role has been authenticated, you can access resources to which they are authorized. You provide resource authorization using resource policies or capability policies, depending on whether you want the user to have control over the resources, or whether you want to override individual user control.
- Audit Everything: Log and monitor both authorized and unauthorized user sessions to your Amazon EC2 instances. It’s essential to integrate AWS CloudTrail and Amazon CloudWatch to monitor all API activity across all AWS instances and your AWS account.
- Storing and Managing Encryption Keys in the Cloud: Security measures that rely on encryption require keys and in an on-premise system, it is essential to keep your keys secure. To manage encryption keys in the cloud, you can leverage server-side encryption with AWS key management and storage capabilities.
SourceFuse’s Business Continuity Planning 101
We ensure a unique value proposition after assessing your potential customer base and go-to-market approach. We tend to build a partnership with our customers by analyzing their needs and identifying the best prospects at the micro-segment level. The next step is the right-sizing of your resources via pay-as-you-go pricing & license inclusion on the basis of ARC (Actual Resource consumption). Our Zero downtime approach coupled with timely delivery enables your business to grow without a pause. 100% Compliance & security is enabled within our AWS Ecosystem. All this and more with our Cloud Migration and Application Modernization Services.
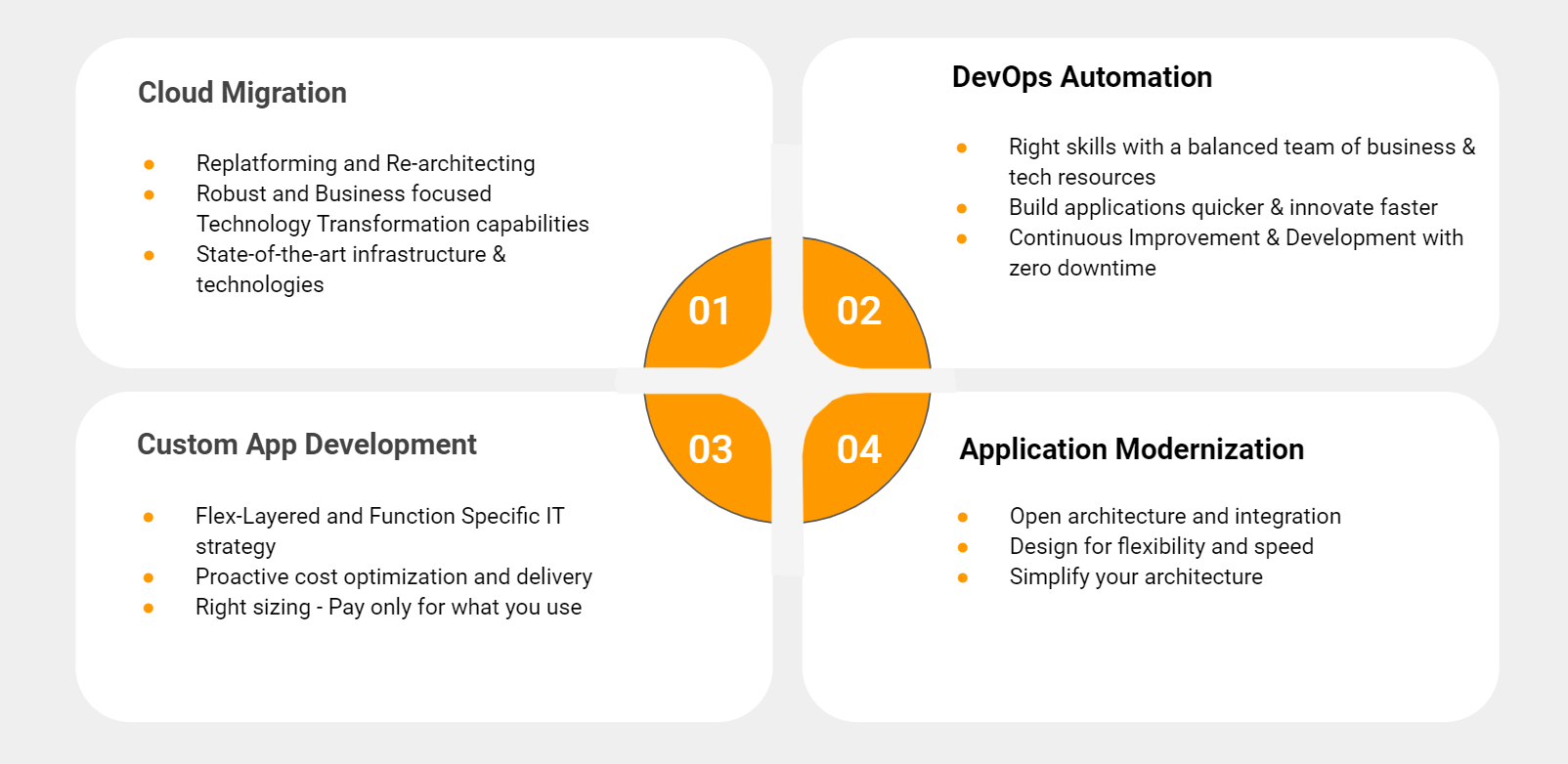
Conclusion:
For SourceFuse, Security and Compliance are the highest priority and we are ensuring that our clients receive our services systematically, even during quarantine. There are vast security capabilities available to users of AWS, and we can help you implement best practices for utilizing those capabilities. Being AWS Advanced Consulting Partners, we leverage AWS platforms/technologies like AWS IAM, AWS Shield, AWS CloudCheckr, AWS CloudTrail to provide HIPAA and GDPR compliant solutions.
Let SourceFuse help you move to the cloud and ease your working from home plan-of-action.